An Integrated, Long-Term Cybersecurity Strategy for Digital Transformation
Digital transformation reshapes how organisations operate through cloud platforms, SaaS, hybrid work and AI-driven workflows. While these changes accelerate innovation, they significantly expand the attack surface. Cybersecurity can no longer be applied after deployment—it must be embedded by design.
Modern threats are persistent, automated and increasingly AI-driven. Attackers simultaneously exploit browsers, misconfigurations, vulnerable systems, network blind spots and human behaviour. Without security integrated into the transformation journey, organisations face heightened breach risk, operational disruption, regulatory exposure and loss of trust. Cybersecurity is therefore foundational to business continuity, data protection and long-term resilience.

Building a Long-Term, Implementable Strategy
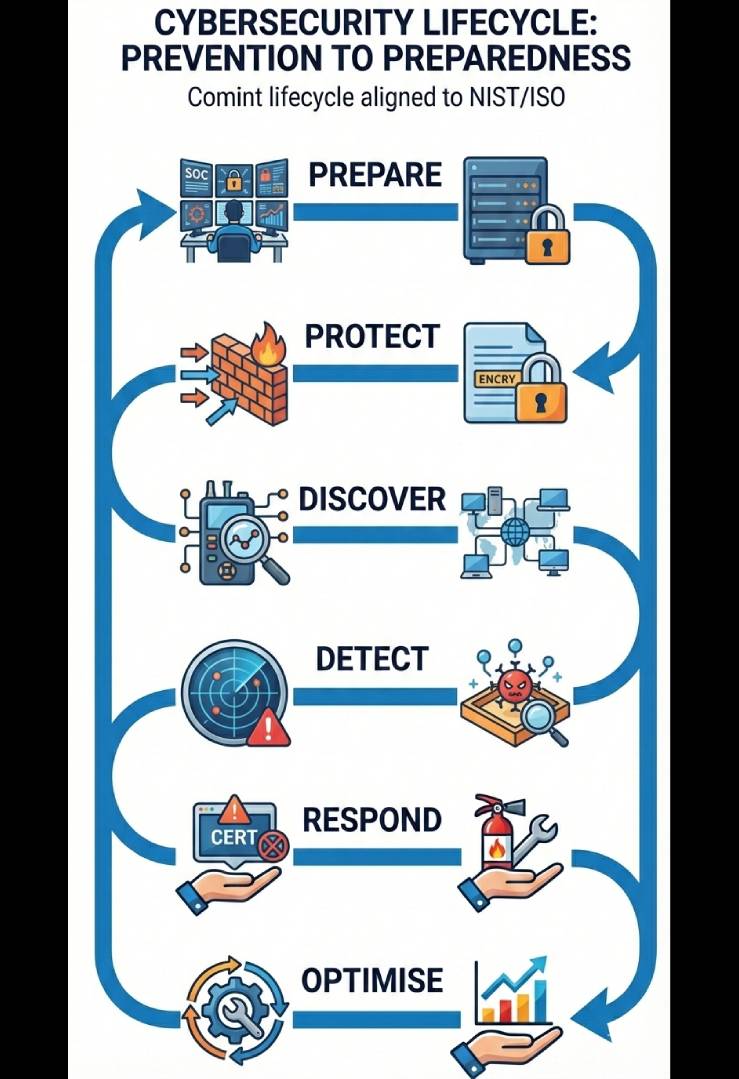
An effective cybersecurity strategy must be continuous, adaptive and implementation-focused. Isolated point solutions create silos and blind spots. Comint follows a lifecycle-driven approach that aligns prevention, continuous risk discovery, rapid detection and response, performance optimisation and operational readiness—ensuring cybersecurity remains practical, measurable and aligned with business outcomes.
Our Integrated Cybersecurity Framework
Comint delivers end-to-end protection through a closed-loop cybersecurity framework:
PROTECT
- Zero-Trust browser isolation blocking phishing, malware, ransomware and zero-day attacks
- Browser data protection with GenAI governance and session visibility
DISCOVER
- Continuous attack-surface and vulnerability visibility across IT and cloud
- Risk-based prioritisation with audit-ready reporting
DETECT
- AI-driven threat detection with NetOps and SecOps context
- Noise-free identification of ransomware, lateral movement and data exfiltration
RESPOND
- Autonomous incident investigation with attack-path and root-cause analysis
- Actionable containment and recovery guidance
OPTIMISE
- Continuous tuning with AI-driven alert and false-positive reduction
- Control validation and risk-based remediation
PREPARE
- Live attack simulations and red-/blue-team exercises
- Measured readiness for incidents, audits and regulators
Together, these capabilities form a resilient, scalable and future-ready security architecture.

Compliance, Governance & Assurance
Compliance and governance are embedded across the security lifecycle. Our approach supports auditability, traceability and regulatory alignment through structured assessments, policy-driven controls, continuous monitoring and documented incident response—helping organisations meet regulatory and contractual obligations while maintaining operational resilience.
Our Cybersecurity Solution Approach & Client Outcomes
As a system integrator, Comint focuses on outcomes—not isolated technologies. We work with proven, best-of-breed cybersecurity partners to deliver integrated solutions while avoiding vendor lock-in. Engagements begin with an end-to-end assessment of the environment, risk posture and compliance needs, followed by the design, integration and optimisation of a tailored cybersecurity architecture aligned to business objectives.
Outcomes for our clients include: reduced cyber risk and faster response, improved compliance and audit readiness, secure high-performing digital operations, confident adoption of cloud and AI, and a sustainable long-term cybersecurity posture.
Modern cybersecurity is not only about isolated tools it is about building a resilient foundation for digital growth.